Keywords
|
| e-banking; e-banking security strategy, e-banking security, e-banking in Zimbabwe, e-commerce |
INTRODUCTION
|
| Advancements in information and communication technology have seen many banks locally and abroad adopting internet or electronic banking in order to remain reverent in this information age. These sentiments were echoed by Chau and Lai (2003) who establish that, in order to sustain business competitiveness, more and more banks are transforming from their traditional approach of “bricks and mortar” into a “clicks and mortar” one under the recent emergence of electronic commerce and business. The banking industry is using this new communication media to offer its customer value added service and convenience. This system of interaction between the consumers and the banking industries is called the electronic or Internet banking system. Federal Financial Institutions Examination Council (2003) defines e-banking as the automated delivery of new and traditional banking products and services directly to customers through electronic, interactive communication channels. The council went on to indicate that, e-banking includes the systems that enable financial institution customers, individuals or businesses, to access accounts, transact business, or obtain information on financial products and services through a public or private network, including the Internet. |
| Business Wire (1995) notes that, the first online banking services based on the Internet were provided by Stanford Federal Credit Union (SFCU) in October 1994. Several authors (Khan et al, 2009; Singhal and Padhmanbhan, 2008) posit that internet banking started with simple functions like real time access to information about interest rate, checking account balances and computing loan eligibility. They further postulate that, these services have graduated to online bill payment, transfer of funds between accounts and cash management services for corporate organizations and individuals. It is clear that as banks expand into internet banking, there is need to focus greater attention to fail-safe security arrangements and systems to safeguard against security threats. This notion is supported by the Federal Financial Institutions Examination Council (FFIEC) that notes that, financial institutions offering Internet-based products and services to their customers should use effective methods to authenticate the identity of customers using those products and services. |
| Supervision and audit of Internet banking will have to be strengthened and vigilance against hackers stepped up. Given these developments, the question that remains unanswered is whether the e-banking security measures in place are effective. |
| The recent launch of broadband internet by Internet Service Providers in Zimbabwe has expanded the availability of internet in the country and it can only mean an accelerated growth in e-banking. E-banking provides easy access and convenience. However, this should not be at the expense and mercy of the security of information. Thus, it is important to deliver a secure e-banking system to avoid the risk of negative effects which include clients accounts being tampered with, phishing or identity theft. This is important in order to ensure the confidentiality of information and that it is not being manipulated or compromised by the fraudsters. Fatima (2011) suggests that, providers of e-banking services must offer more responsive security strategies. |
| In e-banking, funds are transferred through electronic signals between financial institutions, rather than exchange of cash, cheques or other negotiable instruments. In e-banking, Automated Teller Machine (ATM), debit cards, password, and Personal Identification Numbers (PIN) are used for funds transfer. Also, the transfers of funds between financial institutions are recorded on computer systems connected by electronic lines. Customer identification and access to the electronic transaction system is ensured by code, such as password or PIN, instead of a signature on cheques or other documents. |
| Chronicling the history of e-banking in Zimbabwe, Dube, Chitura and Runyowa (2008) posit that, in Zimbabwe, the first visible form of electronic innovation was in the early 1990s when Standard Chartered Bank and Central Africa Building Society (CABS) installed Automated Teller Machines (ATMs). They further indicate that, other forms of electronic innovations that have found their way into Zimbabwean banks are Electronic Funds Transfer Systems (EFT), Telephone banking, Personal Computer (PC) banking and recently internet banking. Along the same lines, Gono (2012) indicates that, in Zimbabwe, Internet banking constitutes 30% of the total retail values. He further notes that, during 2011, internet values increased significantly by 132% to US$532 million from US$230 million in 2010. Regarding mobile banking, Gono (2012) establishes that, in Zimbabwe, there was an increase in the number of banking institutions venturing into mobile banking. He claims that, as at 31 January 2012, fifteen (15) banking institutions had introduced mobile banking products in 43 partnerships with mobile network operators. |
PROBLEM STATEMENT
|
| Insecurity concerns which bedevil e-banking have made some people to criticise this system of banking. As a result of the insecurity, people in e-banking faced the negative incidents of their bank accounts and their transactions being tampered with. These unfavourable experiences have deterred some people from adopting internet banking. Common security features that are currently in place include, ensuring passwords that are at least six characters long and encryption of sensitive data which has brought up several vulnerabilities to both the banks and their clients. This insecurity has been mainly due to the influences of threats like hacking, phishing, transaction poisoning and viruses among others. |
| The existing security strategies have been lacking in terms of privacy, authentication and integrity of transactions hence the need to evaluate and provide remedies that counteract any discrepancies. |
RESEARCH OBJECTIVES
|
| The objectives of this research were: |
| 1. to determine the security strategies that are being used by Commercial banks in Zimbabwe, |
| 2. to determine the impact of different integrated security banking systems on security strategies, |
| 3. to develop a standard metric that is used as a measure for effectiveness of e-banking security strategies, |
| 4. to evaluate the effectiveness of the various e-banking security strategies in Zimbabwe, |
| 5. to recommend solutions to improve the evaluated e-banking security strategies. |
HYPOTHESIS
|
| H0 = Zimbabwean banks are using effective e-banking security strategies. |
| H1 = Zimbabwean banks are not using effective e-banking security strategies. |
LITERATURE REVIEW
|
E-banking defined
|
| The concept of e-banking is a delivery channel for banking services. Banks have been using electronic channels for years to communicate and transact business with both domestic and international customers. Gerrard and Cunningham (2003) have described e-banking as an umbrella term for the process by which a customer may perform banking transactions electronically without visiting a brick and mortar institution. Electronic banking comprises technology enabled banking activities available to a customer through mediums such as the ATMs, websites and so on (Claessens et al., 2002). The characteristics of each environment may differ based on several factors such as the systems, the users and types of transactions. |
| Along with the above definitions, Ganesan and Vivekanandan (2009) define e-banking as the automated delivery of new and traditional banking products and services directly to customers through electronic, interactive communication channels. They further posit that e-Banking includes the systems that enable financial institution customers, individuals or companies to access accounts, transact business, or obtain information on financial products and services through a public or private network, like internet or mobile phone. |
E-banking Security
|
| Several researchers using diverse classification techniques have defined security being a complex concept. Belanger et al. (2002) define security as the protection against security threats. Along with that, Grabner-Krautera and Kaluscha (2003) postulate that, security assures the protection of the two vulnerable points in e-commerce systems, which are the uncertain underlying technological infrastructure and the unreliable users of the system. Kesh et al. (2002) gave a broader definition of the term security wherein they argue that security cannot be defined only as technological measures but to include several non-technical mechanisms such as policies, strategies, information listed on websites and so on. Oscarson (2003) argue that security is primarily composed of a set of security primitives or objectives that are aimed at protecting the systems and/or users against threats. The primary goals of security are Confidentiality, Integrity, Availability, Authentication Authorization, Non-repudiation and Privacy (Kesh et al., 2002). These goals are explained below. |
| According to Suh and Han (2003), confidentiality ensures that the communication between the user or customer and the service provider is not accessible to other parties. Along with that, Knorr and Röhrig (2000) claim that unauthorized access of information should be prevented. The second security goal is integrity. According to Grandison and Sloman (2000), integrity means that during and after information exchange, the content should remain unchanged and should be tamper free. Further to that, Ally and Toleman (2005) indicate that, integrity ensures that content is not created, modified, intercepted or deleted by unauthorized people. The third security goal is availability, which according to Maijala (2004) means that the information required by users should be accessible when required by them. |
| The fourth security goal is authentication. This goal deals with verification of parties who are communicating to guarantee that they are who they claim to be (Maijala, 2004; Suh & Han, 2003). Further to that, Maijala (2004) notes that, authorization which is the fifth security goal, aims to ensure that the user accessing information has the right to view or manipulate this information. The sixth security goal is non-repudiation. This security goal aims to ensure that the party involved in initiating a transaction, sending any information, or receiving any information cannot deny it at a later instance of time (Maijala, 2004). The last security goal is privacy that is defined as the need to guarantee that the customer information is not accessible to unauthorized users and is not misused. |
| According to Cooper (1997) and Daniel (1999), the level of security or risk associated with adoption of e-banking is a major factor affecting the acceptance and adoption of it. Even in countries where electronic banking has long been established, one of the most important factors slowing progress of this new innovation is the consumers concern for security of financial transactions over the Internet and electronic means. An empirical survey by Sathye (1999) of Australian consumers confirmed this fact. Security is one of the very important factors in determining the decision of consumers to use e-banking. Similarly, ABF (1997) found that security concerns are keeping both consumers away from e-banking. Along the same lines, The Walls Report (1997) argues that, unless security is improved, more households would be willing to conduct their transactions over electronic means. |
| In a study, which was conducted in Australia by O’Connel (1996), it was found that security concerns were discovered as the main cause for the slow growth of e-banking in the country. In USA, Thorton Consulting (1996) conducted a survey focusing on banks and concluded that 67 percent of US banks feel that “security strategies” are the major barriers for internet banking. The same results were obtained from the study by Booz et al. (1997) wherein it was revealed that security concern among customers was the top-ranking obstacle for non-adoption of e-banking in Latin America. |
| In view of all these security concerns, this study seeks to evaluate e-banking security strategies and draw conclusions and recommendations on this issue. |
E-banking security loopholes and threats
|
| In electronic commerce, a security threat would be defined as an event that can destroy, modify, waste, deny or disclose information or reduce efficiency of the data and network resources. These threats could appear at the client or the server side (Oppliger, 1999) and these could originate due to human, system or communication errors (Bargh et al., 2002). Egwali (2008) cites several threats like phony items offered for sale, spoofing, phishing scams, identity theft and larceny. Further supporting evidence is provided by Aburrous, Hossain, Dahal, Thabtah (2010), who cited phishing as one form of electronic identity theft. With identity theft, a combination of social engineering and Web site spoofing techniques are used to trick a user into revealing confidential information with economic value. |
| In addition to the above threats, US-CERT (2006) identifies pharming and malware as other e-banking security threats. Additionally, Schneier (2005) claim that, instead of targeting heavily invested bank’s internal systems, the attackers are now targeting the end users’ PCs, which are the weakest link in the network, through various ways such as phishing, key-logger and Trojan horse attacks. Ganesan and Vivekanandan (2009) cite phishing and pharming as the two well-known examples e-banking threats. |
| In a study by BITS (2003), it was established that there are three common forms of internet banking fraud namely identity theft, friendly fraud or fraud committed by a trusted relative or friend and internal fraud which is perpetrated by a financial institution employee. Furthermore, BITS (2003) notes that, there two major threat types which are application and network-based threats. With application threats, the fraudster appears to be a legitimate user of the online banking application, but is instead conducting illegal activities. Security measures such as firewalls, proxy servers, network filters and similar products cannot protect a bank from application-based threats. On the other hand Network-based threats, such as hacks, site-defacement attacks, denial-of-service attacks, and viruses and worms attack the core network and infrastructure but don’t directly try to carry out transactions. Tools such as firewalls can counter these attacks. |
| US-CERT (2006) further posits that, attacks listed above are created using technology, however for them to succeed, they need you to provide information. With phishing attacks, one must provide the information or visit links. With malware, one must be tricked into performing activities they rarely perform and one would have to install the malware on their computer either by running a program, such as an email attachment, or by visiting a web site through email or instant message link. After that, one would have to submit bank details. With pharming attacks, one must open an email, or email attachment and then visit a fake website wherein one will provide information that compromises one’s financial identity (US-CERT, 2006). |
E-banking security strategies
|
| Egwali (2008) and Hawkins et al. (2000) state that, currently, most financial institutions including banks employ security mechanisms such as Secure Socket Layers (SSL), encryption of data that is transferred over the internet, digital certificates, passwords and so forth. |
| Along with that, Claessens et al. (2002) claim that in order to improve the overall security of the e-banking systems, mechanisms such as passwords, policies and so on, have been implemented. Similar comments were made by several researchers including Ally and Toleman (2005), Kesh et al. (2002) and Maijala (2004) who indicate that, each security mechanism implemented strives to achieve a clear security goal such as confidentiality, integrity and so on. Similarly, researchers like Aburrous, Hossain, Dahal, Thabtah (2010) cite SSL as one security mechanism used in e-banking. |
| Apart from the foregoing security strategies, Ganesan and Vivekanandan (2009) propose a secured hybrid architecture model for the e-banking using Hyperelliptic curve cryptosystem and MD5. This hybrid model is implemented with the Hyperelliptic curve cryptosystem (HECC) and it performs the encryption and decryption processes in an efficient way merely with an 80-bit key size. In a study in Brazil by Peotta, Holtz, David, Deus and de Sousa (2011), several security models were discussed notably, Digital Certificates, One-Time Password Tokens, One-Time Password Cards, Browser Protection, Virtual Keyboards, Device Registering, CAPTCHA Short Message Service (SMS), Device Identification, Positive Identification, Pass-Phrase and Transaction Monitoring. |
Cases of E-banking Threats
|
| Literature is loaded with cases of e-banking threats. Fatima (2011) gives several examples of internet banking fraud. Some of the examples include, the $10 million computer fraud against Citibank, the Internet bank Egg case in Britain and the fire alarm company in Arkansas which lost more than $110,000 when hackers stole the firm’s online banking credentials and drained its payroll account. Other cases include the Nigerian Advances fee fraud or 419, as they are commonly known (Amedu, 2005). |
| In addition to the above cases, Bank (2005) reported on how a US Military Academy at West Point found that more than 80% of its cadets succumbed to a phishing attack by a fictional colonel. Similarly, the State of New York mounted two attacks on its 10,000 employees; 15% were spoofed by the first attack, but only 8% by the second, which came three months later. A study by Anti-Phishing Working Group (2006), confirmed that about eight out of ten respondents have visited a spoofed web site and over 15% provided personal data to a spoofed site. Avivah (2004) conducted a user study and found that about two million users revealed sensitive information to spoofed web sites, and estimate a loss of about 1.2 billion$ to credit card issuers and U.S. banks in the year 2003. |
METHODOLOGY
|
| The study followed a descriptive design technique. A descriptive research intends to present facts concerning the nature and status of e-banking security strategies, as it exists at the time of the study. The target population composed 15 commercial banks that provide the four (4) e-banking functions namely; ATMs, Points of Sale, Internet banking and Mobile banking in Harare, Zimbabwe. To give a fair representation of the total population, each of the fifteen (15) Commercial banks were included. Thus, our target population was equal to the sample size. We dealt with the IT and E-Banking departments in the various Commercial banks because those were the central points of reference. |
| Sixty questionnaires were evenly distributed at an average of four questionnaires per bank within the fifteen banks. Survey questionnaires were designed and delivered to respective banking personnel such as IT and security managers, e-banking managers, system administrators, security assurance specialists and IT Auditors. The questionnaires consisted of both qualitative and quantitative questions that were open ended and close ended. |
| A bipolar five point Likert scale was incorporated in the survey questionnaires to optimize the research methodology. The null hypothesis stated that Zimbabwean banks are using effective e-banking security strategies. Contrary, the alternative hypothesis stated that Zimbabwean banks are not using effective e-banking security strategies. The hypotheses were tested at 95% level of significance using a two tailed Student’s T test. The null hypothesis was only to be rejected if the value of the modulus of Student’s T calculation was less than the value of Student’s T tabulated at n-1 degrees of freedom. All data collected was fed into the Statistical Package for the Social Sciences (SPSS) for analysis and output values interpreted using standardized metrics. |
DATA PRESENTATION AND ANALYSIS
|
| Of the 60 questionnaires which were distributed at an average of 4 questionnaires per bank in 15 banks, only 31 were filled, and 2 returned blank giving a total of 33 returns. Therefore, the questionnaire response rate was 51.7%.The corresponding data was then analysed using SPSS. |
Empirical Results
|
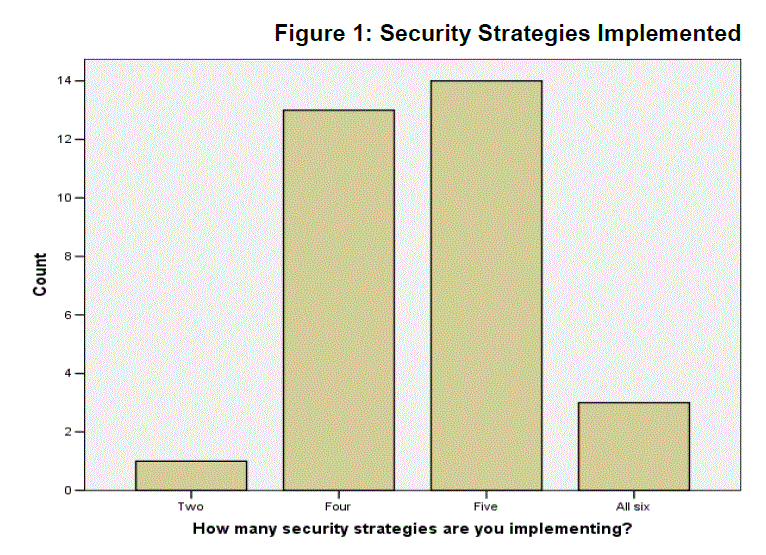
| As evidenced by Figure 1 below, most banks are using between four and five e-banking security strategies from strategies including passwords, firewalls, encryption, virtual keyboards, pins and access codes and Secure Socket Layers. |
| Figure 1 above depicts that security in Zimbabwean Commercial banks is highly prioritized thus the effectiveness of these strategies is of paramount importance as that interrelate with their usage. Each of the strategies has a competitive edge with respect to e-banking security hence all are summarized and analyzed. |
| Table 1 below shows a 100% positive response with respect to passwords demystifies that entry level passwords are basic security features for e-banking transactions practiced by all Zimbabwean commercial banks. Strong dependence in firewall usage was observed with the exception of two commercial banks which optimized firewall security on their security modules within their integrated banking systems. |
| Likewise, encryption is a very much prevalent security strategy. Only a small minority is not implementing encryption. Contrary, the majority of Zimbabwean commercial banks are not utilizing virtual keyboards as an e-banking security strategy. This strategy is relatively new to Zimbabwe and most e-banking personnel showed ignorance to the strategy. With respect to PIN and Access Codes, the table depicts a very high implementation of the respective security strategy. However, sophisticated strategies such as SSL are averagely implemented by Zimbabwean commercial banks as evidenced by the above results. |
| All security strategies being implemented are resident on one of the following Integrated Banking System application: Globus, Flexcube, Equation and Primsoft. A relationship exists between e-banking security strategies and the Integrated Banking System. Thus, Integrated Banking Systems have an impact on e-banking security strategies. Figure 2 below shows the prevalence of each banking system within Zimbabwean Commercial banks. |
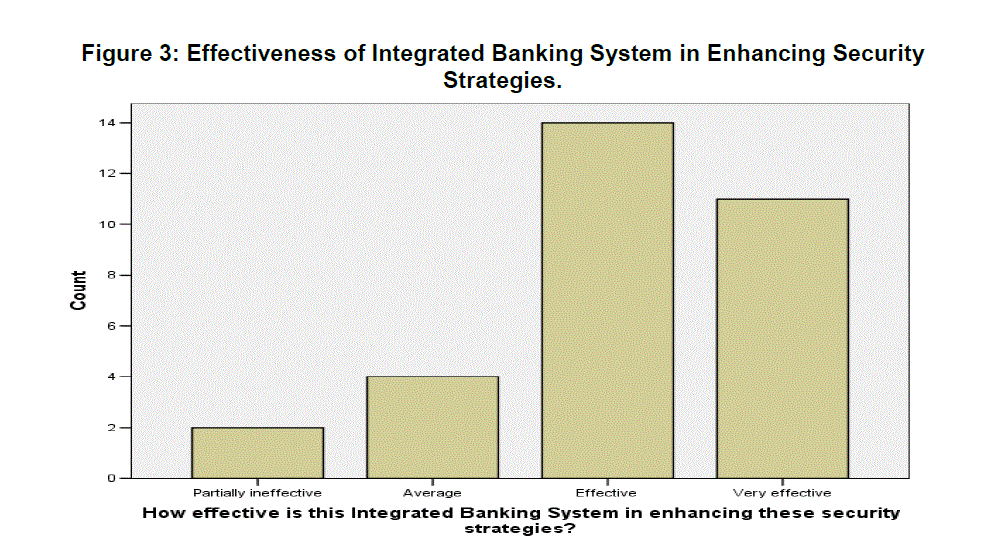
| Effective implementation of these Integrated banking systems enhances e-banking security strategies hence an assessment was done to ascertain the level of implementation. Figure 3 below summarizes the findings. The graph below ascertains the effective implementation of Integrated banking Systems which in turn have a strong positive correlation with e-banking security strategies. |
| Without loss of generality, Table 2 below depicts that security strategies currently implemented are effective. At least 60% of the valid responses cited that the security strategies have been at least effective basing on that there have been no threats of fraudulent activity and absolutely no cases of hackings in most banks in the country hence the highest response being on effective. |
Hypothesis testing
|
| Our sample population constitutes less than 30 Zimbabwean commercial banks and standard deviation is unknown hence the Student’s T test was implemented. The hypothesis was expressed as follows: |
| H0: Zimbabwean banks are using effective e-banking security strategies. |
| H1: Zimbabwean banks are not using effective e-banking security strategies. |
| A two tailed test at 95% level of significance with n-1 degrees of freedom was performed. The rejection criterion was: Reject H0 if Tcal = Ttab. The test statistic was, Ttab = 2.353363. Table 3 below shows figures used to calculate the composite mean value of 3.84, which is not equal to the Ttab value of 2.353363. The decision is to accept the null hypothesis and conclude that we are 95% confident that Zimbabwean banks are using effective e-banking security strategies. |
DISCUSSION
|
| Ganesan and Vivekanandan (2009) described a secured hybrid architecture model for the e-banking using a cryptosystem. This model contains a number of secure layers with several authenticity levels that tallies with our findings. This is so because, most respondents implemented this as a way of advancing or improving the effectiveness of e-banking security strategies. Hutchinson & Warren, (2003) explained that as e-banking falls under the spectrum of e-commerce applications they must also fulfill the same set of security requirements to aid to the strategies that will be implemented which has been evidenced in this paper. |
| Hawkins et al. (2000) states that, currently most financial institutions including banks employ security mechanisms such as Secure Socket Layers (SSL), encryption of data that is transferred over the internet, digital certificates, etc. To protect customer information stored within their servers, most financial institutions use firewalls, virus detection and protection methods, backup servers as some of the protective measures. This gives a strong base for the result that banks in Zimbabwe are implementing effective e-banking security strategies. This has again been testified by our research findings. Overall, the research reveals that Zimbabwean commercial banks are implementing secure and effective hybrid of e-banking security strategies which include passwords, firewalls, encryption, virtual keyboards, pins and access codes and Secure Socket Layers. This contradicts with findings by Fatima (2011) who cites several examples of e-banking related frauds implying that the security strategies which were being used were not effective. |
CONCLUSION
|
| This research evaluated the effectiveness of e-banking strategies being used by commercial banks in Zimbabwe. From the results presented in the foregoing section, the following conclusions were drawn, Firstly, e-banking security strategies implemented in Zimbabwean Commercial banks include; encryption, password authentication, firewalls, Secure Socket Layer (SSL) and Virtual Keyboards. Secondly, from our five point Likert scale, the evaluation proved an effective implementation of the above e-banking security strategies. Thirdly, Integrated banking systems such as Globus, Flexcube, Primesoft and Equation enhanced the effectiveness of these e-banking security strategies. However, only 19.4% of the commercial banks implemented virtual keyboards. Thus a few banks in the e-banking arena, due to very expensive installation, adopted this model. Ultimately, Zimbabwean Commercial Banks were prioritizing e-banking security and were confident regarding currently implemented strategies. |
RECOMMENDATIONS
|
| E-banking is a very critical area which should always be abreast with current trends in technology so as to minimize phishing and internet identity theft. The augmentation of eye recognition, Hybrid Token Systems and USB keys with current implemented strategies will enhance security for electronic transactions. In addition to that, the implementation of shielded authentication that is not vulnerable to web spoofing should be practiced by respective commercial banking sites. The employment of fingerprint authentication merged with graphical models that incorporate one-time authentication mechanisms would be effective against both offline and online spoofing attacks. |
| The banks need to conduct constant educational programs for e-banking users alerting them on how to always ensure a secure online transaction. The Central bank of Zimbabwe should further lower e-banking service charges as a way of cultivating increased usage by clients. If the above attributes are implemented in unison, then security strategies implementation will improve from being effective to very effective. Thus, client trust and confidence will be greatly boosted. In addition to that, another research. |
| “A study on customer perspective in relation to security in e-banking transactions in Zimbabwean Commercial banks”, will further demystify the customer’s perspective regarding e-banking security. |
Tables at a glance
|
|
|
| |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
|
| |
References
|
- ABF. (1997). Banks Approach Market with Caution. Australian Banking and Finance, 6(13), 9-11.
- Aburrous M., Hossain M. A., Dahal K., and Thabtah F. (2010). Experimental Case Studies for Investigating E-Banking Phishing Techniques and Attack Strategies, Springer Science+Business Media, 2, 242–253
- Ally, M., &Toleman, M. (2005). A framework for assessing payment security mechanisms and security information on e-commerce web sites. 9th Pacific Asia Conference on Information Systems (PACIS), Bangkok, Thailand.
- Amedu, U. M. (2005). Domestic electronic payment in Nigeria: The challenges. Central Bank of Nigeria Bullion, 29(1).
- Anti-Phishing Working Group (2006). Phishing Activity Trends Report, January.
- Avivah L. (2003). Phishing Attack Victims Likely Targets for Identity Theft, Gartner FirstTake, FT-22-8873, Gartner Research, 4 May 2004.
- Bank, D. (2005). ‘Spear Phishing’ Tests Educate People About Online Scams. The Wall Street Journal, August 17, 2005.
- Bargh, M., Janssen, W., &Smit, A. (2002). Trust and Security in E-business Transactions. Retrieved 08 August, 2012, from http://scholar.google.com/url?sa=U&q=https://doc.telin.nl/dscgi/ds.py/Get/File-22996/TIpaperWWW2002final_1.pdf
- Bélanger, F., Hiller, J. and Smith, W.J. (2002). Trustworthiness in electronic commerce: The role of privacy, security, and site attributes. Journal of Strategic Information Systems, 2(3/4), 245-270.
- BITS (2003). Fraud prevention strategies for internet banking, bits fraud reduction steering committee, Washington DC.
- Booz, Allen and Hamilton (1997). Internet banking: a global study of potential. Booz, Allen & Hamilton Inc., New York, NY.
- Business Wire (1995). Stanford federal credit union pioneers online financial services. Business Wire, June 21.
- Cooper, R.G. (1997). Examining some myths about new product winners, in Katz, R., ed., The human side of managing technological innovation, Oxford, 550-560.
- Chau, P., and Lai, V. (2003). An empirical investigation of the determinants of user acceptance of internet banking. Journal of Organizational Computing and Electronic Commerce, 13 (2), 123-145.
- Claessens, J., Dem, V., Cock, D. D., Preneel, B. &Vandewalle J. (2002). On the security of today’s online electronic banking systems. Computers & Security, 21 (3), 257-269.
- Daniel, E., (1999). Provision of Electronic Banking in the UK and the Republic of Ireland. The International Journal of Bank Marketing, 17(2), 72-82.
- Dube, T., Chitura, T., and Runyowa, L. (2008). Adoption and use of internet banking in Zimbabwe: An exploratory study. Journal of Internet Banking and Commerce, 14 (1).
- Egwali, A. O. (2008). Customer Perception of Security Indicators in Online Banking Sites in Nigeria. Journal of Internet Banking and Commerce,13(3).
- Fatima A., (2011). E-banking security issues – Is there a solution in biometrics? Journal of Internet Banking and Commerce, 16 (2).
- Federal Financial Institutions Examination Council (2003), E-Banking Booklet.
- JIBC December 2012, vol. 17, no.3 - 16 -
- Ganesan, R., and Vivekanandan, K. (2009). A secured hybrid architecture model for internet banking (e-banking). Journal of Internet Banking and Commerce, 14 (1), 1-17.
- Gerrard, P., and Cunningham, J. B. (2003). The diffusion of internet banking among Singapore consumers. International Journal of Bank Marketing, 21(1), 16 – 28.
- Gono, G. (2012). Monetary policy statement. Reserve Bank of Zimbabwe, Harare.
- Grabner-Krauter, S., and Kaluscha, E. A. (2003). Empirical research in on-line trust: a review and critical assessment, International Journal of Human-Computer Studies, 58, 783-812.
- Grandison, T., and Sloman, M. (2000). A survey of trust in Internet Applications. IEEE. Retrieved 08 August http://www.comsoc.org/pubs/surveys/.
- Hawkins, S.,Yen, D.C., & Chou, D.C. (2000). Awareness and challenges of internet security. Information Management and computer security,8(3),131-143
- Hutchinson, D. and Warren, M. (2003). Security for internet banking: a framework. Logistics Information Management, 16 (1), 64-73.
- Kesh, S., Ramanujan, S., and Nerur, S. (2002). A framework for analyzing e-commerce security. Information Management and Computer Security, 10(4),149-158.
- Khan, M. S., Mahapatra S. S., and Sreekrumah (2009). Service quality evaluation in internet banking: An empirical study in India. International Journal of Indian Culture and Business Management, 2(1), 30 – 46.
- Knorr, K., &Röhrig, S. (2000). Security of electronic business applications: structure and quantification. Paper presented at the proceedings of the First International Conference on Electronic Commerce and Web Technologies.
- Maijala, V. (2004). Outlook of the information security in e-business. Retrieved 8th August, 2012, from www.tml.tkk.fi/Publications/Thesis/maijala.pdf#
- O’Connell, B. (1996). Australian Banking on the Internet- Fact or Fiction? The Australian Banker, (December),212-214.
- Oppliger, R., and House, A. (1996) Authentication systems for Secure networks. Retrieved 8th August, 2012, from www.artech-house.com
- Oscarson, P. (2003). Information security fundamentals, graphical conceptualisations for understanding: research group VITS, Department of Business Administration, Economics, Statistics and Informatics, Örebro University, Sweden.
- Peotta, L., Holtz, M.D., David, B.M., Deus, F.G., de Sousa, R.T. (2011). A Formal Classification of Internet Banking Attacks and Vulnerabilities. International Journal of Computer Science & Information Technology, 3 (1).
- Sathye, M.(1999). Adoption of Internet Banking by Australian Consumers: An Empirical Investigation. International Journal of Bank Marketing, 17(7), 324-334.
- Schneier, B. (2005). Two-factor authentication.Too little, too late, Communications of the ACM,48(4),136.
- Singhal, D., and Padhmanabhan V. (2008). A study on customer perception towards internet banking: Identifying major contributing factors. The Journal of Nepalese Business Studies, V (1), 101 – 111.
- Suh, B., and Han, I.(2002). Effects of trust on customer acceptance of Internet banking. Electronic Commerce Research and Applications, 1, 247-263.
- Thorton, C. (1996). Thorton consulting online banking: a success. Australian Banking and Finance, 5(13), 2.
- US-CERT (2006). Banking Securely Online. Retrieved from: http://www.us- cert.gov/reading_room/Banking_Securely_Online07102006.pdf
|